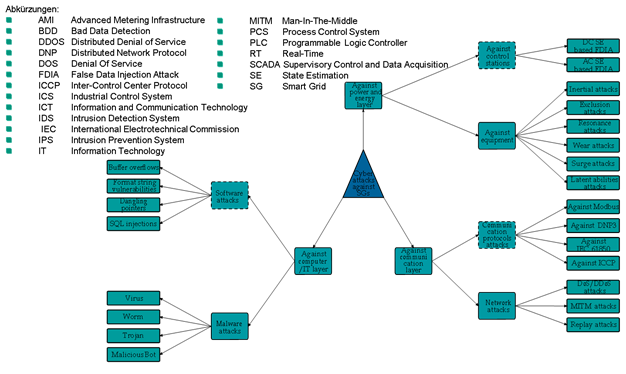
Weak point analysis in energy system protocols
Norms and standards defining the network communication infrastructures for automation systems and in particular for energy systems were not initially developed with security in mind.
Several attack scenarios such as Man-In-The-Middle (MITM), False Data Injection Attack (FDIA) and Denial-of-Service can be implemented and that might result in instabilities in the energy system under the existing real-time requirements.
To better analyze the vulnerabilities of the some of the protocols, used in the energy sector such as Generic Object Oriented Substation Event (GOOSE), Sampled Values (SV) and Manufacturing Message Specification (MMS) and the standards recommendations such as IEC 62351, a cost-efficient testbed to simulate the communication network of an IEC 61850 electrical substations was developed. Different experiments using the testbed were implemented in order to analyze the communication behavior.
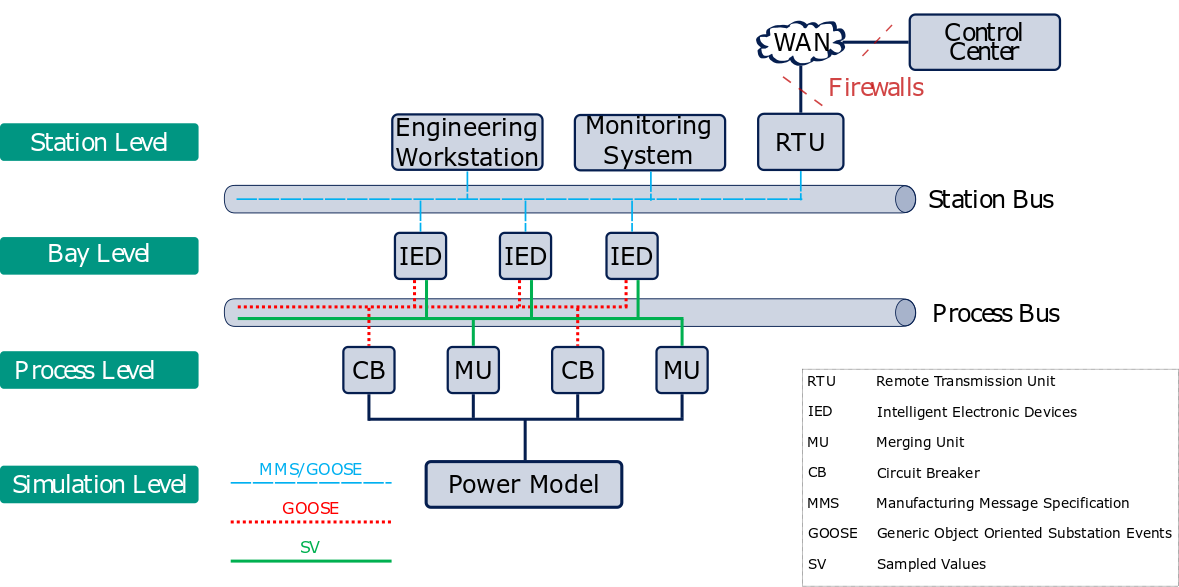
As a result of previous work, specific attack vectors for electrical substations based on IEC 61850 were identified as well general attack vectors in the energy systems of the future.