Alarm Correlation Based on Risk Assessment Process in Energy Systems
- Contact:
- Project Group:
- Funding:
HGF POF IV
- Startdate:
2021
- Enddate:
2025
The results of the risk assessment are crucial, since the process improves the understanding of the sources and nature of the risks. This research project will mainly concentrate on the context establishment, risk identification, risk analysis, and risk evaluation steps of the risk assessment. Security Information and Event Management (SIEM) system allows managing, collecting, analyzing and correlating a huge amount of security events in a centralized system. Therefore, when considering prevention, detection and reaction process against growing threats in SGs, a SIEM system is evaluated as an efficient and helpful tool. However, SIEM systems have still open research challenges in terms of executing alarm correlation that is based on a comprehensive risk assessment process. Besides, there is a need for widely adaptation of the IEC 62351-7 standard, that defines several Network and System Management (NSM) data objects to support mainly the health of a device or network in a realistic IEC 61850 substation. While some research has been carried out the implementation of alarm correlation with i.e. Bayesian network, similarity-based alarm correlation or methods based on IP address’ correlation; there is still need for further scientific understanding to implement an effective alarm correlation framework based on risk assessment process. Developing an effective alarm correlation framework that is based on a comprehensive risk assessment process will amplify risk awareness, help to understand risk sources, support engineers and/or operators to reduce the number of alerts, and mitigate risks in the further steps. Additionally it can be integrated in a SIEM system. The general representation of the suggested framework is illustrated in Figure 1.
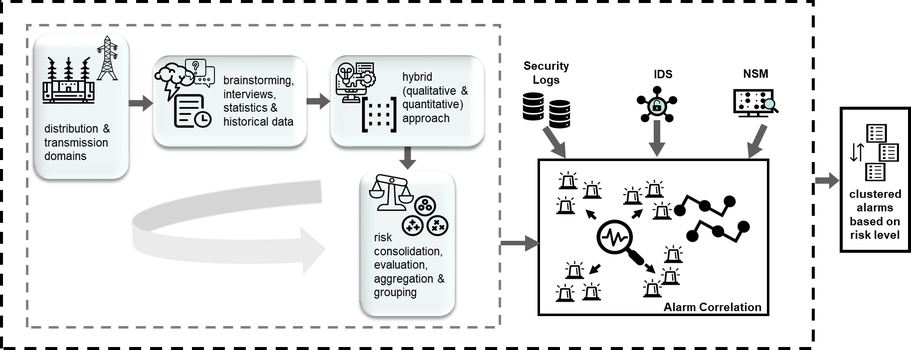
In this research, realistic scenarios considering normal operation and feasible attack scenarios will be performed to enhance the risk analysis including the quantification technique. With the implementation of these relevant scenarios, logs and alarms will be collected from various devices and levels. The risk assessment can be conducted as qualitative, quantitative or hybrid. In order to obtain more precise evaluations, a hybrid approach will be developed within the scope of this research project. Arising security concerns, investigating which part of the SG is under risk and at which level, integrating recommendations from the IEC 62351-7 standard and ultimately supporting decision-making process are the main expected outcomes from this research project. This will be achieved by addressing the aforementioned questions and overcoming the explored challenges.

