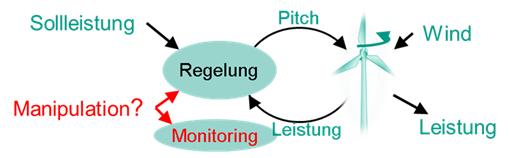
In model-based anomaly detection, the aim is to use status data to identify whether individual components in the system have been manipulated. Attacks using false data injection exploit the fact that the corrupted commands and data are syntactically and semantically correct, but do not match the current system state. In this way, the system is feigned to be in the wrong state and the system brings itself into highly critical limits, which leads to damage or even destruction of the system.