Intrusion Response on Energy Systems, Mitigation and Recovery
- Contact:
- Project Group:
- Funding:
HGF POF IV
- Startdate:
2021
- Enddate:
2025
Control operations in energy systems (ESs) contain interactions between cyber and physical domains. Use of open computation and communication platforms as well as complex systems in ESs introduce various vulnerabilities. These vulnerabilities can be exploited by attackers to damage mentioned infrastructures, e.g. deception attacks can compromise the integrity in ESs by modifying the measurements sent from sensors and/or the control commands used for updating the physical processes.
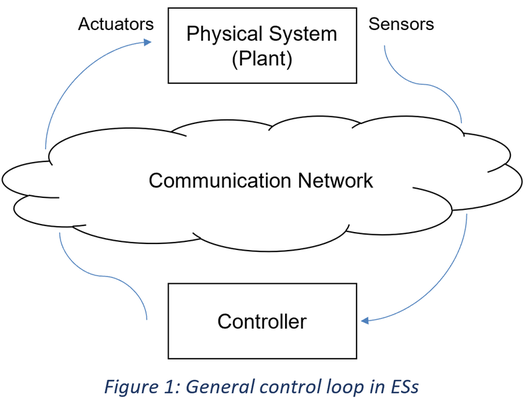
Various defense mechanisms have been studied in order to counter these attacks, which are commonly classified in three categories: protection, detection, and mitigation.
Methods of detecting cyber-attacks on control systems and their isolation (also known as identification) have been widely investigated in the literature (in detection, the goal is to uncover an anomaly in the system caused by a cyber-attack. In isolation, on the other hand, the goal is to identify where the anomaly occurs). But the response and mitigation of these attacks has relatively received less attention and the response usually remains a manual process. In addition, existing mitigation methods have some limitations, such as lack of scalability or inability to deal with false alarms generated by Intrusion Detection Systems (IDSs).
Therefore, it is required to develop an approach that can compensate for these limitations. This gap in the literature is used as motivation to develop a response mechanism for mitigating the effects of these attacks.
This general concept of the mechanism can be based on estimating of the states of the physical system (plant). Any false alarms that might be generated by the anomaly detection and isolation process should be suppressed. Then a recovery mechanism tries to restore the correct information modified by attackers. Methods based on machine learning can also be used to recover the correct information. With correct information, the system can then operate under safe conditions.
The overall concept of such a mechanism is still being explored and more ideas may be developed during the project progress. A general layout of the system is demonstrated below:
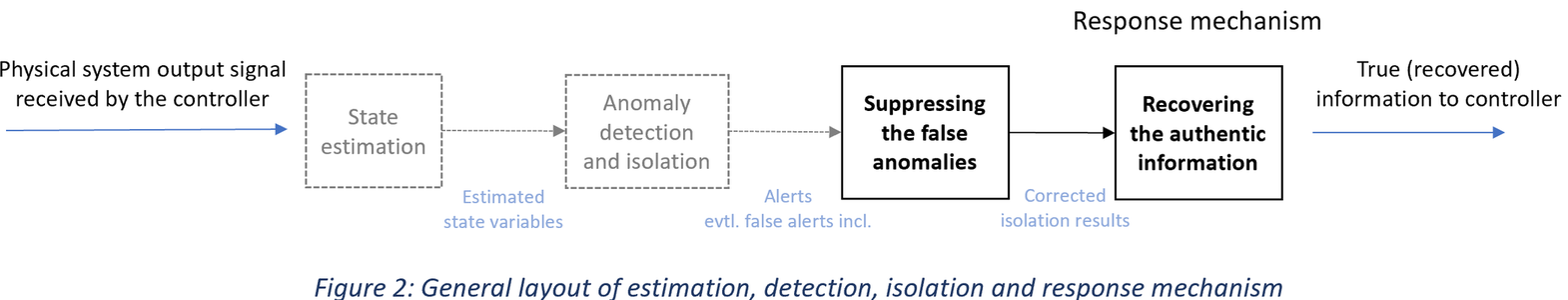
Effectiveness of the developed mechanism will be investigated within the KASTEL Security Research Labs using physical system simulation models where various attack scenarios hindering the integrity such as False Data Injection Attacks will be implemented.

