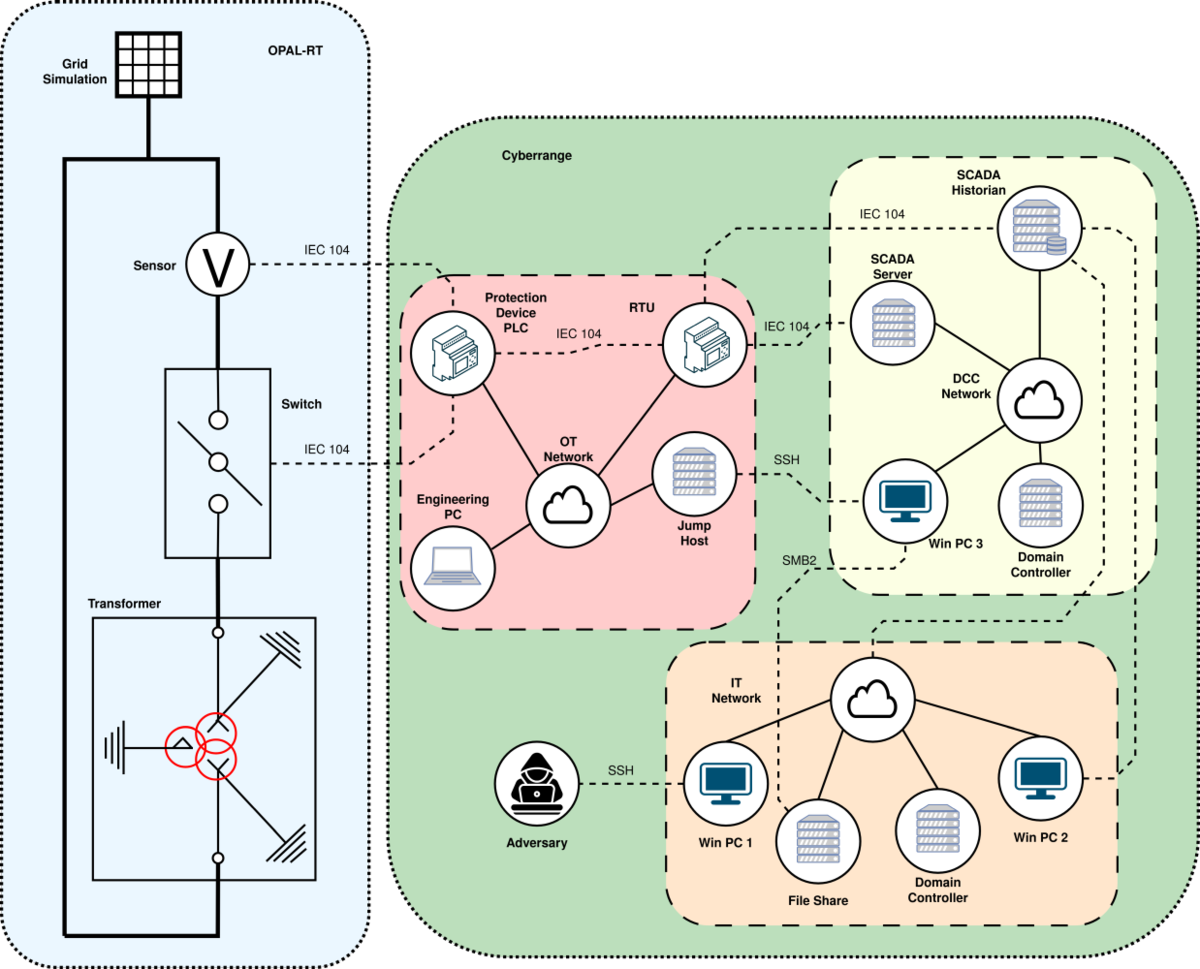
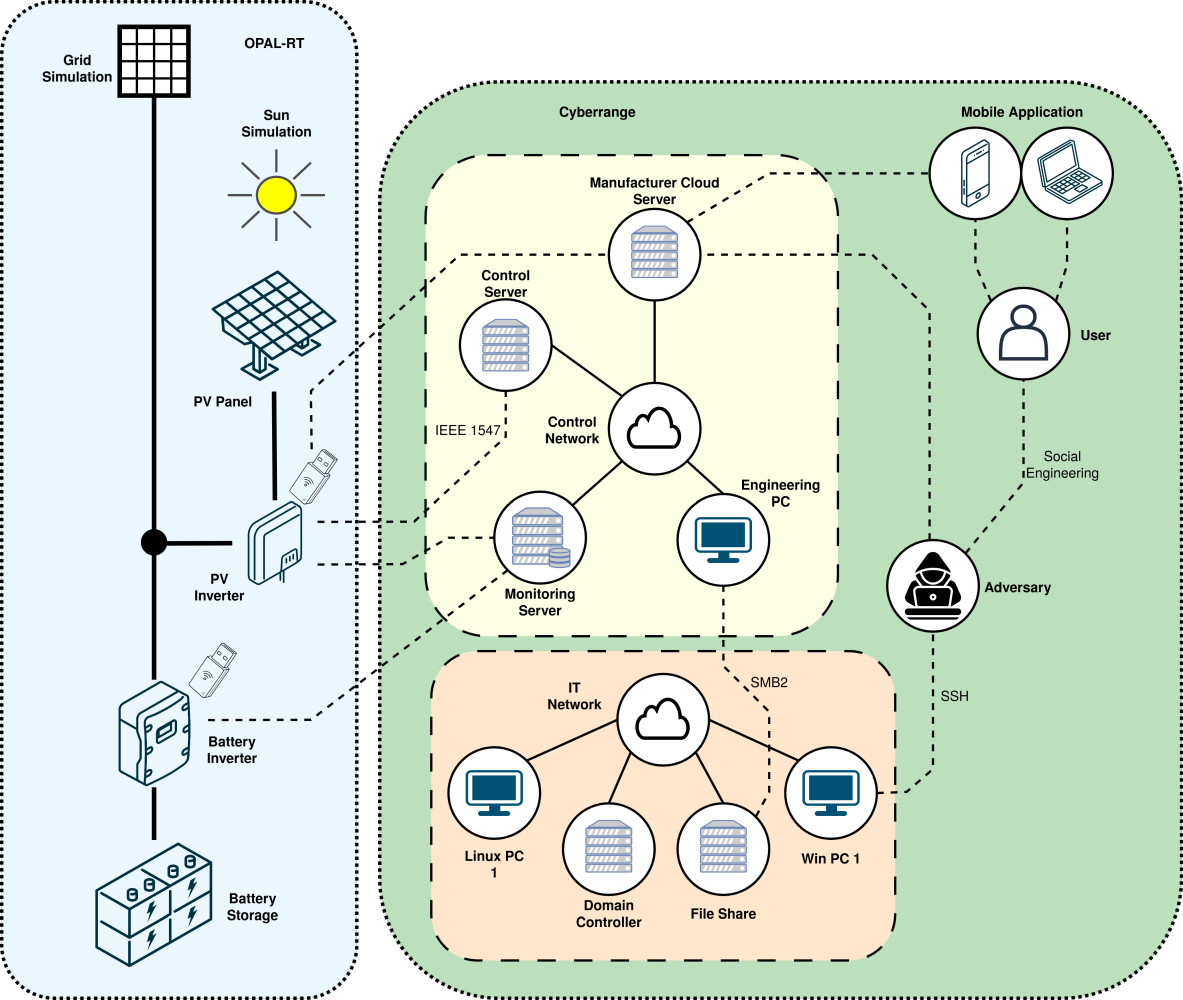
Building upon the individual projects of our research group, an overarching goal of the working group is to carry out and record real and realistic cyberattacks on energy infrastructures and components completely end-to-end. The beginning of a cyberattack refers to the initial intrusion and compromise of a system, for example through phishing or social engineering, and is generally referred to as the ”initial compromise”. Starting from an initially compromised system, an attacker will typically enumerate, explore, and eventually compromise further networks, servers, and computers, until a target system is reached or another effect has been achieved. In the process, information and data may be exfiltrated (data leakage), and the boundaries of different networks and domains may be crossed. The end of a cyberattack refers to the physical impacts that an attacker aims to cause in the target system, for example opening the busbars in all affected substations, remotely controlling photovoltaic inverters and influencing the regulation of the power grid, or damaging a transformer and thereby causing its subsequent failure.
Our capabilities in the areas of cyberattack emulation, simulation of electrical engineering systems with real-time simulations, as well as our Cyber Range, are combined for this purpose. The attacks are carried out in a realistic and complete manner and recorded in the greatest detail, so that the data can be used for testing attack detection systems and by the scientific community.