In recent years, there has been a growing number of cyberattacks by nation-state actors, known as Advanced Persistent Threats (APTs), targeting critical and energy infrastructures. APT attacks differ from ”ordinary” threats in that they are often highly complex and executed over extended periods of time. Additionally, state-sponsored attackers typically have substantial resources at their disposal, enabling the development of specialized firmware and malware.
For research and evaluation of detection approaches for APT attacks, researchers rely on datasets that contain records of such attacks. However, the number of suitable datasets that include attacks with APT-like characteristics is very limited. Furthermore, existing literature has repeatedly criticized the quality of these datasets, both in terms of data and the attacks themselves. As a result, many researchers implement and record their own attacks for evaluation purposes but do not publish the resulting data. This leads to problems with the comparability of evaluations of APT attack detection methods. The Cyber Range project aims to close this gap.
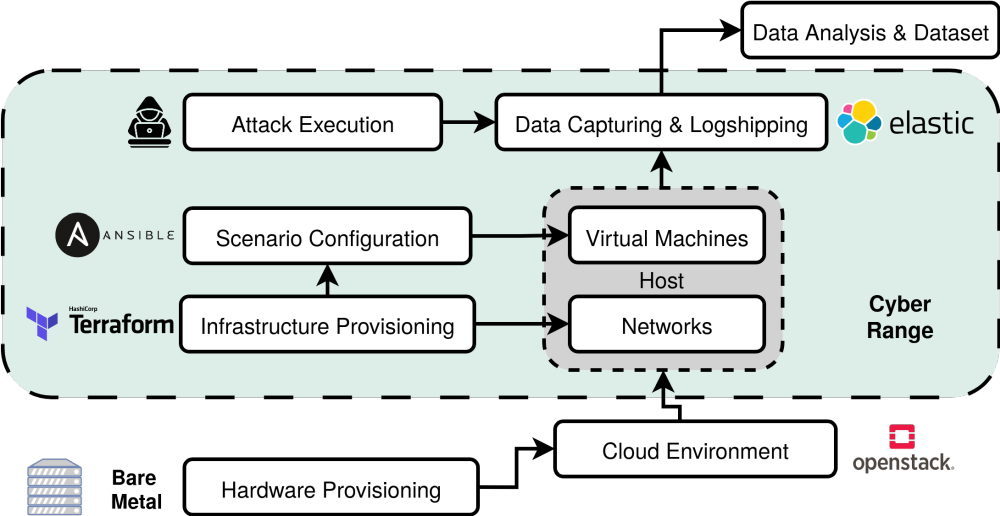
Our Cyber Range is designed to replicate and record attack scenarios and known APT attacks in a realistic infrastructure. This is made possible because the Cyber Range is entirely virtual thanks to various virtualisation technologies, and is therefore independent of the rest of the institute’s infrastructure. Infrastructures and scenarios can also be reconstructed accurately with minimal effort and time. Moreover, the Cyber Range can operate completely independently of personal user accounts, eliminating the need to anonymize data before publication.
Overall, the Cyber Range is a building block towards the overarching goal of fully emulating cyberattacks from start to finish—beginning with the initial intrusion on the IT side and extending to the physical impacts on the OT side. OT systems are to be simulated up to Level 2 of the Purdue Model for industrial control systems. By emulating and meticulously recording known APT attacks, the project aims to create a high-quality dataset for APT attack detection research. In addition to general APT attacks, the focus will also be on attacks specifically targeting energy systems. The integration of IT and OT emulation within this project is another particularly noteworthy aspect.